Get Started
Use these developer guides to learn how to integrate your organization with Branch using our API endpoints. Use the buttons above or the menu at the left to navigate to the topics you're interested in.
If you want to jump right in using the Branch API, follow these steps to get started. If you're not a Branch partner yet, click here to contact us and learn how to become one.
Set up your sandbox
The first thing you'll want to do is make test API requests using the sandbox environment,
which allows you to simulate users and wallets without going through background checks or using real data.
Once you have your sandbox API key and Org ID you're ready to start. You'll have separate API keys for sandbox and production, which you can read about here.
Walkthrough: Create an employee
The Try It feature in this developer documentation is a simple way to make API requests to the sandbox. Let's walk through using it to create a new employee:
- Navigate to the reference page for the Create Employee endpoint.
- Enter your Org ID in the field.
- Enter an ID for your new employee. We're choosing 100116.
- Under BODY PARAMS, enter a first and last name for the employee.
- Enter a phone number and an email address. None of this has to be real information, since this is the sandbox.
- For this example, leave the other fields blank until you come to the api key field.
- Under HEADERS in the field labeled apikey, enter your org sandbox API key.
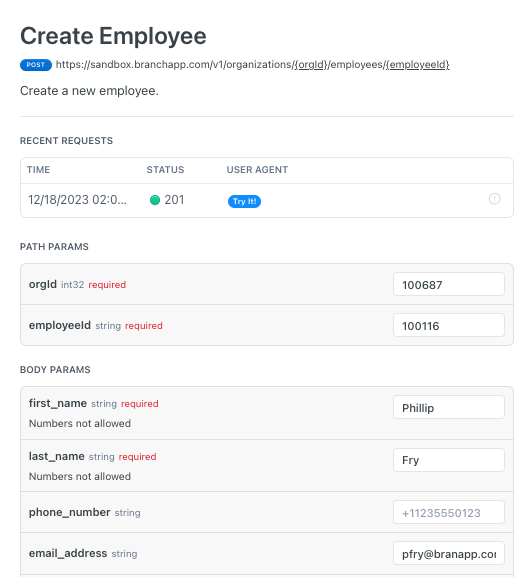
- Click the button labeled Try It at the right. If the request is successful you receive a response similar to what you see in the RESPONSE box in this image:
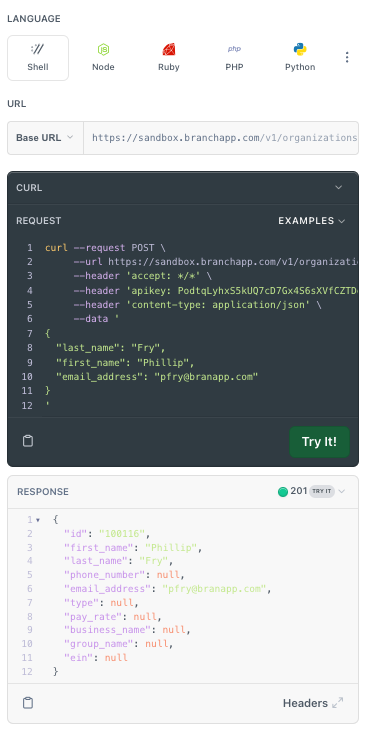
The response code shows you that you've created an employee with the name, address and other information you provided.
In the dark box above the response, you can see an example of the code for the request, in this case showing the code in cURL. This code was assembled from the data you entered in the fields to the left.
To see what the code would be in other programming languages, select the buttons labeled Node, C++, Python, and so on. This makes it easy to copy and paste the code to integrate it into your system. Here is the code that you see if you click the Ruby button:
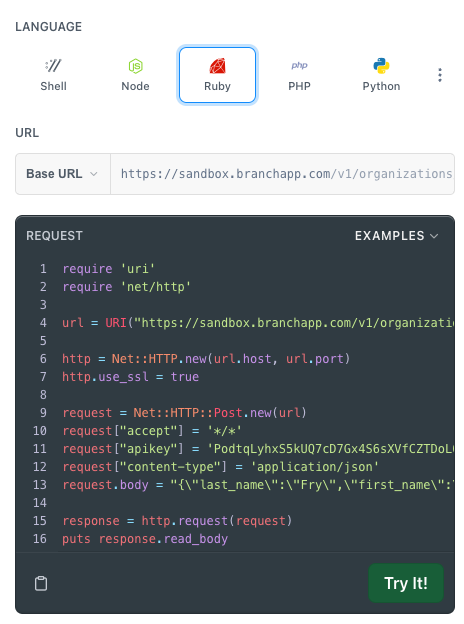
Test your integration using the sandbox and your API key.
Learn how to:
Build your Branch Integration
Branch will schedule a kickoff call with key business and technical stakeholders from your org and your Branch partnership team.
Gather requirements and design integration, get Branch approval.
Get access to the Branch sandbox environment including a sandbox-only API key.
Build your integration, including setting up and testing webhooks using the sandbox environment. For an example of steps for testing webhook sandbox-only functionality see webhook sandbox testing
Use the sandbox to develop and test integrating your system with Branch API endpoints and webhooks. The API endpoints and webhooks involved depend on which onboarding approach you use, for details see onboard workers.
Branch will supply test cases and your org will provide recorded demos for each scenario.
Testing is asynchronous when possible.
Your org must be certified by Branch in each environment before promoting to the next (Sandbox -> UAT -> Production).
Deploy your integration
Receive API key and access to the Branch production environment.
Align on key deployment dates with Branch.
Branch recommends a Beta release for 2 to 3 weeks before general availability.
For more about Branch and becoming a partner, see these links:
Read the product descriptions.
Request a free demo
Become a Branch Partner
Updated about 2 months ago
